Secure Web 2.0 (& Drupal) Part 6
A7 Missing Functional Level Access Control
Most web applications verify function level access rights before making that functionality visible in the UI. However, applications need to perform the same access control checks on the server when each function is accessed. If requests are not verified, attackers will be able to forge requests in order to access functionality without proper authorization.
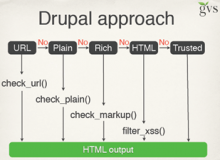
Drupal approach:
· Menu system uses access callback and access arguments
· Continually review permissions