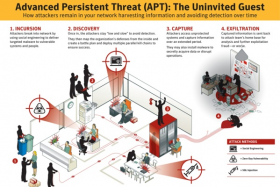
- General (and Institutional) Introduction:-http://www.ieee-security.org/TC/SP2013/posters/Mordehai_Guri.pdf
- Case Study Analysis: http://www.alienvault.com/blog-content/2011/09/Fighting-Advanced-Persistent-Threats-APT-with-Open-Source-Tools.pdf
- APT Attacks: https://media.blackhat.com/us-13/US-13-Yarochkin-In-Depth-Analysis-of-Escalated-APT-Attacks-WP.pdf
- Tool WebSite: https://www.virustotal.com
APT changes the approach of currently performing Security Assessment. Indeed, the way of conducting such an analysis changed over the time:
- In '80s and '90s, it was based on VA and PT, mainly; making use of trusted methodology, like OSSTMM.
- In '00s, when the Web 2.0 was introduced, Web Application PT should be addedd, adopting OWASP Testing Guide
- In '10s, APT become pervasive, also the Threat Assessment should be count in.
In order to forecast the effects of APT exploit in a company infrastructure, an assessment based solely on vulnerabilities (wheather TCP-IP, HTML, etc) residing in server systems (a few, in numbers) is not sufficient. The clients (many) are now addressed.
In order to make countermeasures manageable, a proper threat assessment should be conducted. Here a White Paper from Gartner "Threat Assessment in the Age of the APT:
https://www.gartner.com/doc/2738617/threat-assessment-age-apt
- APT Detection: http://www.verint.com/solutions/communications-cyber-intelligence/solutions/cyber-security/advanced-persistent-threats-apt-detection/index
- APT Anomlay: http://nigesecurityguy.wordpress.com/2014/03/19/apt-anomaly-detection-part-1/
- APT Indicators: http://nigesecurityguy.wordpress.com/2014/01/10/apt-detection-indicators-part-2/
- APT Prevention (Red Teams analogous to "Tiger Team" for counteracting previous IT threats): http://nigesecurityguy.wordpress.com/2014/01/08/apt-red-teams-part-1/