CMS Solutions
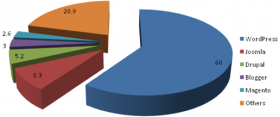
According to [1], the top three used product are: WordPress, Joomla! and Drupal. Everyone of these has proper pros and cons. The following graph depicts CMS usage during 2014, according to WebcomWebsites (http://www.webcomwebsites.co.uk/our-articles/ ):

In the following, WordPress, Joomla! and Drupal will be addressed, by security point of view.
CMS Security
CMS Security could be defined in a 5W-1H fashion, like in the following table. A fast comparison between WP,
Joomla! and Drupal was presented (see notes row):
|
5W1H |
Description |
Notes |
|
|
5W1H |
Issue |
Description |
Notes |
|
Who |
Secure Core Code |
Code inspected by the Security Team, in order to assure the CMS Kernel is secure by itself. |
|
|
What |
Module Development |
Security issues are statically checked by formal verification: · Core Security Check · Proactive Approach: 3rd party formal testing of posted modules |
Drupal only |
|
Where |
Security Categories |
The Security issues fall into one of the following categories: 1. Core Code (CMS Kernel) 2. 3rd party Extension (Modules, Plug-ins, Themes) 3. Custom per-Site (current implementation) 4. Admin Configuration 5. Environment (e.g. physical server, O.S., web server, DB, etc) |
|
|
When |
Access Control |
Security issues are dynamically checked by revision of accessmechanisms: · Granular · Role System |
Drupal only |
|
Why |
Security Issues |
Security issues could involve one of the following: · Secure Code · Access Control · Content Security |
|
|
How |
Tackling Security |
In order to avoid security issues, the following countermeasures and stadards are implemented: · Security Team · Object Interface · 3rd party Integration |
Easy Rules for CMS Protection
Here 5 simple rules for protecting the CMS:
1. Update and Patch CMS at a regular schedule
2. Backup CMS and underlying DB weekly
3. Subscribe to List and Forum about CMS vulnrablities
4. Change default usernames (e.g. “admin”) and use strong password
5. Double check additional components (plug-ins, modules) before installing them
Security Breaches
- Million WordPress websites vulnerable to DOM-based XSS
http://securityaffairs.co/wordpress/36607/hacking/million-wordpress-dom-based-xss.html
- WordPress: FBI Warns About ISIS-Themed Defacement
http://news.softpedia.com/news/FBI-Warns-About-ISIS-Themed-Defacement-Urges-WordPress-Admins-to-
Patch-477974.shtml
- CMS-Made-Simple (2007-09-13)
http://www.cmsmadesimple.org/cgblog/794/cmsmadesimple-org-defacement/
- SPIP: Santa Cecilia (2015-03-04)
Comments
Secure web 2.0 continued
Secure web 2.0 continued